VxLAN support added in 7.0beta5
MikroTik announced VxLAN support on Valentine’s Day (Feb 14th) of 2020.
This is a significant feature addition for RouterOSv7 as it will pave the way for a number of other additions like EVPN in BGP.
It will also give MikroTik the ability to appeal to enterprises and data centers that might need cost-effective VxLAN capable devices.
Service Providers are also moving towards VxLAN as a future replacement for VPLS so this is helpful for that market as well.
Download the OVA here:
https://download.mikrotik.com/routeros/7.0beta5/chr-7.0beta5.ova
Implementation
The initial release of VxLAN is based on unicast and multicast to deliver Layer 2 frames.
As there is no EVPN support, the VTEPs must be manually configured for each endpoint in a full mesh configuration.
The VxLAN interface can then be bridged to a physical ethernet port or VLAN interface to deliver the traffic to the end host.
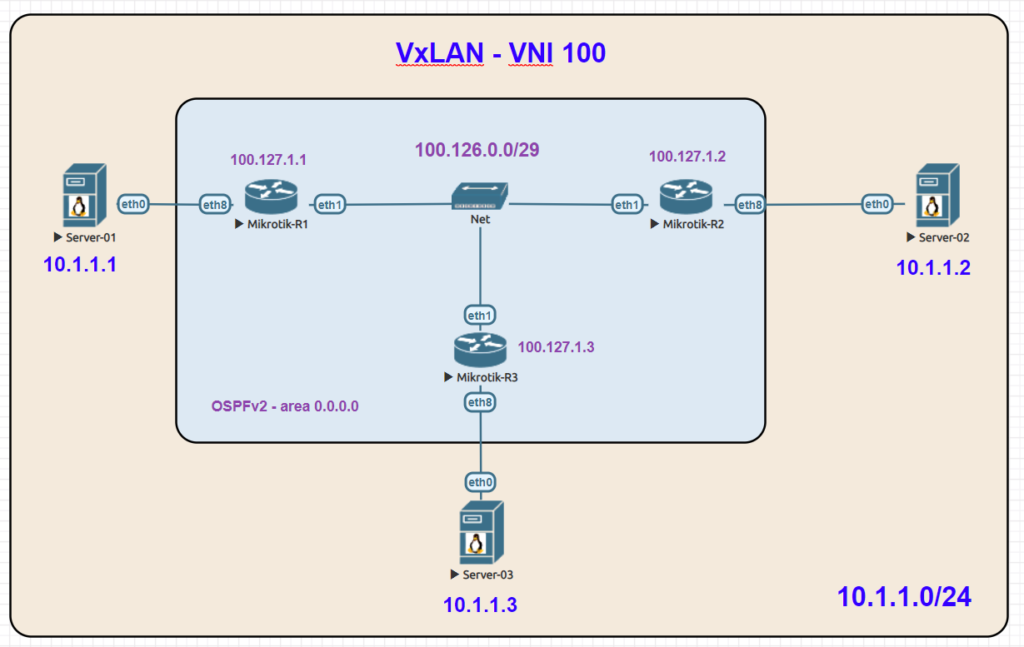
Lab Example
Here is an overview lab in EVE-NG with a basic setup using 3 linux servers on the same 10.1.1.0/24 subnet which is carried as an overlay by VxLAN.
VxLAN reachability for VTEPs is acheived with OSPFv2 and loopback addresses.
VNI: 100
Multicast Group: 239.0.0.1
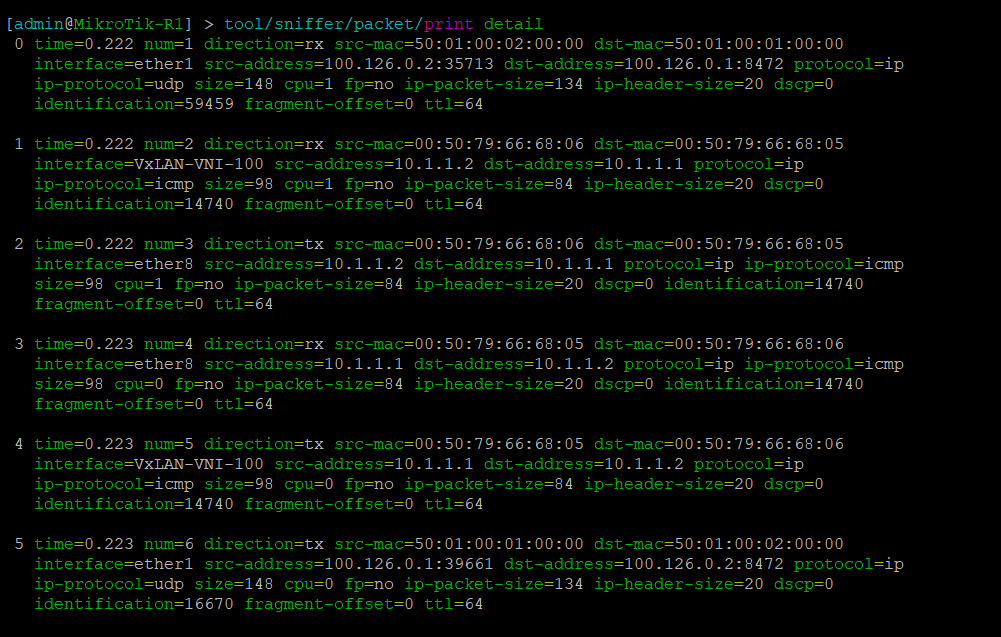
Lab Validation
In the following packet capture, traffic to UDP port 8472 can be seen between two endpoints.
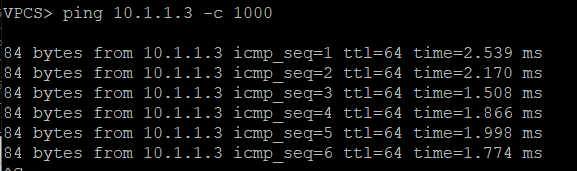
The ICMP ping test between server 1 (10.1.1.1) and server 2 (10.1.1.2) is also visible
Pings between Server 1 and Servers 2 & 3
Configurations
R1
/interface bridge add name=Bridge-VxLAN-VNI-100 add name=Lo0 /interface vxlan add group=239.0.0.1 interface=ether1 mtu=1400 name=VxLAN-VNI-100 port=8472 vni=100 /routing ospf instance add name=ospf-instance-1 router-id=100.127.1.1 version=2 /routing ospf area add area-id=0.0.0.0 instance=ospf-instance-1 name=ospf-area-1 /interface bridge port add bridge=Bridge-VxLAN-VNI-100 interface=ether8 add bridge=Bridge-VxLAN-VNI-100 interface=VxLAN-VNI-100 /interface vxlan vteps add interface=VxLAN-VNI-100 remote-ip=100.127.1.2 add interface=VxLAN-VNI-100 remote-ip=100.127.1.3 /ip address add address=100.127.1.1 interface=Lo0 network=100.127.1.1 add address=100.126.0.1/29 interface=ether1 network=100.126.0.0 /routing ospf interface add area=ospf-area-1 instance-id=0 network=100.126.0.0/29 add area=ospf-area-1 instance-id=0 network=100.127.1.1 /system identity set name=MikroTik-R1
R2
/interface bridge add name=Bridge-VxLAN-VNI-100 add name=Lo0 /interface vxlan add group=239.0.0.1 interface=ether1 mtu=1400 name=VxLAN-VNI-100 port=8472 vni=100 /routing ospf instance add name=ospf-instance-1 router-id=100.127.1.2 version=2 /routing ospf area add area-id=0.0.0.0 instance=ospf-instance-1 name=ospf-area-1 /interface bridge port add bridge=Bridge-VxLAN-VNI-100 interface=ether8 add bridge=Bridge-VxLAN-VNI-100 interface=VxLAN-VNI-100 /interface vxlan vteps add interface=VxLAN-VNI-100 remote-ip=100.127.1.1 add interface=VxLAN-VNI-100 remote-ip=100.127.1.3 /ip address add address=100.127.1.2 interface=Lo0 network=100.127.1.2 add address=100.126.0.2/29 interface=ether1 network=100.126.0.0 /routing ospf interface add area=ospf-area-1 instance-id=0 network=100.126.0.0/29 add area=ospf-area-1 instance-id=0 network=100.127.1.2 /system identity set name=MikroTik-R2
R3
/interface bridge
add name=Bridge-VxLAN-VNI-100
add name=Lo0
/interface vxlan
add group=239.0.0.1 interface=ether1 mtu=1400 name=VxLAN-VNI-100 port=8472
vni=100
/routing ospf instance
add name=ospf-instance-1 router-id=100.127.1.3 version=2
/routing ospf area
add area-id=0.0.0.0 instance=ospf-instance-1 name=ospf-area-1
/interface bridge port
add bridge=Bridge-VxLAN-VNI-100 interface=ether8
add bridge=Bridge-VxLAN-VNI-100 interface=VxLAN-VNI-100
/interface vxlan vteps
add interface=VxLAN-VNI-100 remote-ip=100.127.1.1
add interface=VxLAN-VNI-100 remote-ip=100.127.1.2
/ip address
add address=100.127.1.3 interface=Lo0 network=100.127.1.3
add address=100.126.0.3/29 interface=ether1 network=100.126.0.0
/routing ospf interface
add area=ospf-area-1 instance-id=0 network=100.126.0.0/29
add area=ospf-area-1 instance-id=0 network=100.127.1.3
/system identity
set name=MikroTik-R3
What is the benefit of vxlan over eg. vtp tunneling over ospf/bgp routing and mpls?
The mtu size seems even worse. ;-/
sorry, ment vpls. not vtp, too late in the evening. 😉
It can handle BUM traffic in more efficient way (encapsulated inside IP multicast) instead of copying such traffic multiple times to other endpoints. It requires properly working multicast routing to work. Unfortunately it doesn’t solve CE multihoming issues as pure VXLAN is still based on hardware mac learning on VTEPs. Such problems (and many others like anycast gateways or LACP distributed across IP fabric) can be solved if used in conjunction with EVPN based control plane. I hope mikrotik guys are working on this.
VxLAN solves a number of scale and loop avoidance issues that VPLS has. It also does not require LDP or other MPLS signalling and can work over IP.
Also, you can use a 1500 byte MTU, you just have to adjust the IP MTU on the transit links. I was building the lab quickly and just lowered the tunnel but you can certainly use a larger MTU if the equipment supports it.
This because of RouterOS in virtual, so you cant set MTU 1500.
i hope this feature long time,it’s great, i use RouteOS ten years old.
You mention unicast:
> The initial release of VxLAN is based on unicast and multicast to deliver Layer 2 frames.
I can’t see how to configure that, is it possible, or is it only multicast at present?
Thanks for the Post Kevin.
Have you tried the VxLAN over PPPoE? I see currently the VxLAN uses multicast, can this be changed to Unicast?
Good functionnality at last ! And good article.
Is VXLAN would be the swiss knife in front of L3-MPLS / EVPN and current WAN-based enterprises connectivities ?
Does it have chance to be really largely adopted ?
Thanks
Hi,
I rebuild your example in my lab and I can still ping my servers without configured vteps.
Why?
What about VxLAN over IPSec?
How does VxLAN scale on Mikrotik devices? How many VTEPs can be defined, is there a performance penalty after a certain amount of entries? Can it encapsulate tagged packets without issue?
Looking to replace a Q in Q (mostly 15+ year old Cisco) based metro area network (mostly fiber based with a few 5GHz links and a couple VPN over outside carrier links) and eliminate such fun that as PVST and VTP and upgrade links from 1Gbps everywhere to 10Gbps for most links and 40 Gbps between cores. It’s a municipal government network and funding is a challenge at the moment, MikroTik CRS line looks promising on switching performance, but have to wonder if it’s “too good to be true”.
From my understanding VxLAN in handled in the switch ASIC and not the CPU on the CRS line, correct?
Hi to all,
What is the default gateway of server ?
There is no default gateway needed here because his servers are all on the same network, so its layer 2 which is what vlxan is for. Gateways are only needed if you need to reach a destination outside your network, eg routed. If his example included that, then the gateways would be at your leaf.