.
Funding a new WISP
There are a number of ways to fund a startup Wireless Internet Service Provider (WISP), but the two we most commonly see are self-funded by individuals/partners or by leveraging private equity (PE) money.
Private equity has become increasingly popular in the last few years if we are to use our consulting clients as a basis for comparison.
It’s not hard to see why, while you can (and many do) start a WISP on a shoestring budget, getting a significant chunk of initial funding to cover the costs of tower construction/leasing, network equipment, sales/marketing, etc is very attractive as it allows a WISP to build a network that might otherwise take several years of organic growth to achieve.
Network Engineering – the missing ingredient
Many startup WISPs are often borne out of necessity – fast, reliable or economical Internet access – one or more of these is missing in the areas we see WISPs develop.
Typically the stakeholders come from a variety of backgrounds some of which are technical and some aren’t – all of them, however, share a vision of building out Internet access and solving problems that are unique to their corner of the world.
Out of that group, probably less than 5% come out of the ranks of professional network engineers.
And this isn’t to say that you need to be a network engineer to start a successful WISP, quite the contrary, the most successful WISPs are formed by people who understand what a well-run business looks like.
But when you’re in the business of building and selling access to a service provider IP network, at some point, you will benefit from having a network engineer as part of your team – whether that happens in the beginning or down the road is the core focus of this article.
.
Build it and then fix it
Build it and then fix it later is probably the most common approach when it comes to the network design of a new WISP. Many startups (understandably) want to save money anywhere they can – consultants or tech labor costs can be steep when money is only going out and not coming in.
“Let’s just get it up and running so we can get some revenue and then we’ll fix things”
I’ve probably heard this phrase uttered a few hundred times when working with startup WISPs over the last decade.
This is the main reason bridged networks are so commonly found in startup WISPs. The network engineering is far simpler when everything is a single network and broadcast domain.
And it’s easy to see the allure of this approach – No subnetting, VLANs, routing protocols or advanced protocols like MPLS are required.
However, this is often the beginning of a painful journey for many WISPs that will result in an initial network redesign somewhere between 500 to 1000 subscribers as the broadcast domain will reach a point where performance starts to suffer and the mad dash to fix it begins.
The cost of redesign
Network redesigns are costly in the form of equipment, labor, downtime and lost opportunities. One of the key pieces of advice we give to prospective clients whether we work for them or not is to get someone that is a network professional involved with the network design from day one – whether it’s a consultant or an in house network engineer.
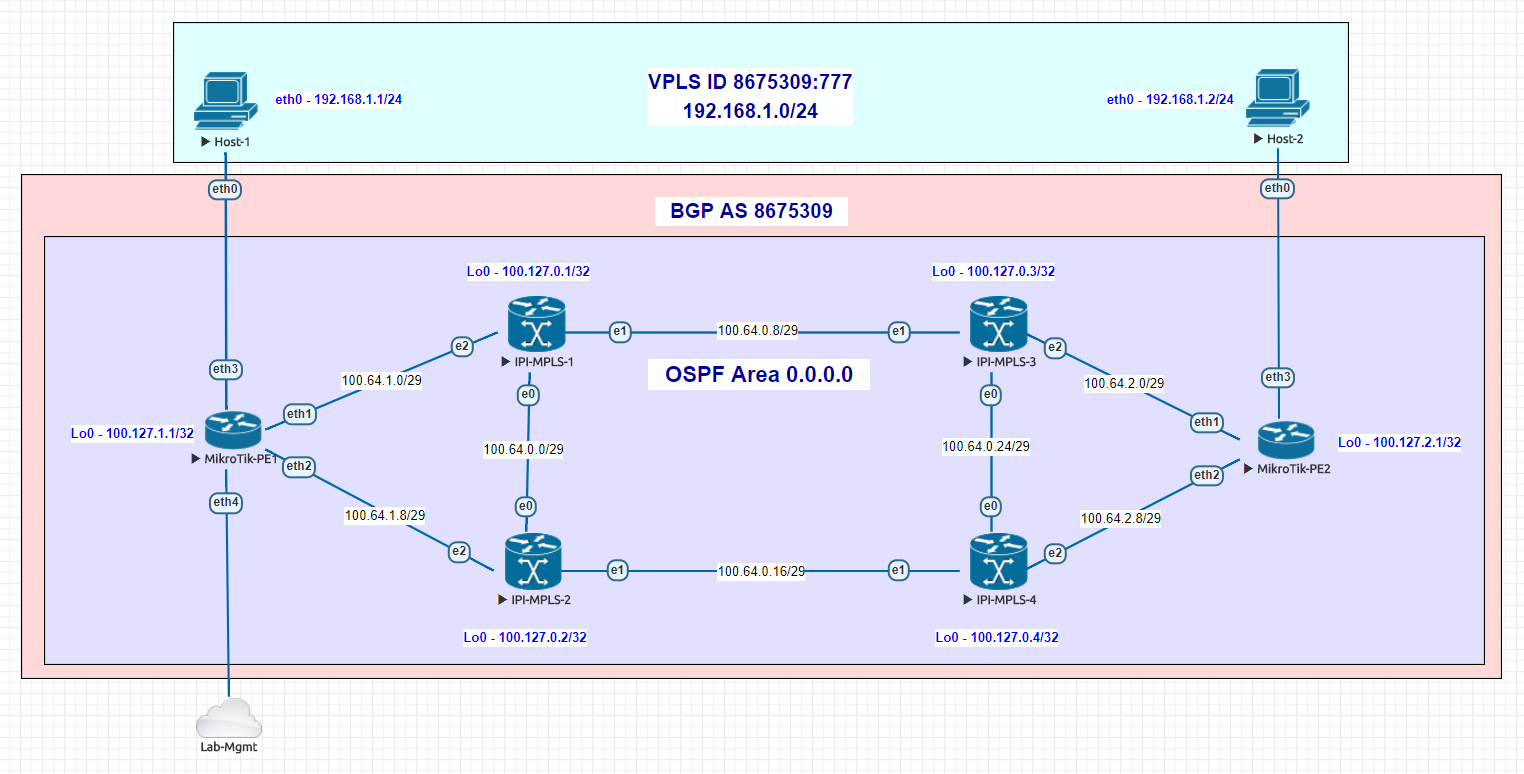
When we come in and perform a network redesign, there will be elements we use common to most ISP networks like:
- A Subnet/VLAN plan that allows for both growth at a tower and scaling of multiple towers
- Use of an IPAM/DCIM like Netbox
- When to use RFC 1918 and 6598 IP space vs. Public IP space
- IPv4/IPv6 and CGN
- Capacity planning – what speeds and feeds are needed now and in the future
- L2/L3 design for Data Centers/PoPs
- L2/L3 design for towers and aggregation networks
- Routing architecture design that includes an IGP like OSPF along with BGP and MPLS
- Planning for Billing, DNS, DHCP and other services.
- Security and DDoS planning
Typically, the response we get from most clients is something like “wow, I wish I’d known about all of this before I started and just done it on day one – it would have been cheaper”
The cost of going through the redesign exercise can be substantial, even for a very small WISP, it can exceed $10k and for larger WISPs, it can easily be $100k or more.
It might seem like the list above is fairly complex for a very small network with only one tower and one Internet feed, but the reality is that if you build a design that’s ready to scale and template on day one, it will be far easier to grow quickly and not have to forklift those components in at a later date with large out of pocket costs.
.
How does Private Equity fit in?
When getting private equity firms to fund a new WISP, there are a number of budget items that go into the business plan but a plan to hire network engineers or consultants is rarely among them…why?
Many of the stakeholders involved in WISPs are often savvy tech people that are able to learn and digest new things quickly. I believe there is a perception that it’s less costly to start with a simplistic network design using the existing team and learn ‘on the fly’ rather than hire an experienced networker as a consultant or especially as an employee.
Before I get too much hate mail, there are plenty of success stories of WISPs that were built from the ground up that had to learn on the fly and were able to build a great network – so i’m not trying to paint a picture that it can’t ever be done.
The trial and error approach has a better chance of succeeding when you’re self-funded as you can gauge when you need help instead of getting hammered by investors when the network isn’t working well.
Private equity firms, however, are looking for a predictable return on their investment and skipping proper network design and planning with an experienced professional often puts a huge dent in the projected ROI for a number of reasons like:
- Poor network performance which leads to slow or even negative subscriber growth
- Higher install and truck roll costs due to the use of non-standardized and validated templates for subscribers
- Network redesign costs
- Outages due to lack of HA design
- Excessive purchase of equipment due to lack of formal capacity planning and understanding of equipment use cases.
And the list keeps going. These are just a few of the real-world examples we have seen that get categorized as “unforeseen costs.”
Experience is the key for investors to controlling costs and building a reliable production network that will produce a consistent ROI.
The key takeaway here for private equity firms and entrepreneurs that are seeking money via PE is to get professional network engineering incorporated into the budget at the beginning to minimize the list of “unforseen costs” in the first 180 to 365 days of network operation.
Whether you hire a consulting firm or a a full or part time network engineer to assist with this step, the key is to get someone who has experience with ISP operations and design – with WISPs especially.
The money saved from using a design validated by a professional will be likely be substantial and rapid growth is far easier when the network is built right from the beginning – both of these put the PE Firm and the WISP Owner/Operators in a great position to succeed and return value to investors in a shorter amount of time.