About the Cisco to MikroTik series
One of the most difficult configuration challenges for MikroTik equipment seems to be switching and VLANs in the CRS series. Admittedly, the revamp of VLAN configuration for MikroTik CRS switches in early 2018 made things a lot easier. But, sometimes there is still confusion on how to configure VLANs and IP addresses in VLANs with MikroTik RouterOS operating on a switch.
This will only cover VLAN configuration for CRS 3xx series switches in RouterOS as SwitchOS is not nearly as common in operational deployments.
CRS 1xx/2xx series use an older style of configuration and seem to be on the way out so I’m not 100% sure whether or not i’ll write a similar guide on that series.
If you’ve been in networking for a while, you probably started with learning the Cisco CLI. Therefore, it is helpful to compare the commands if you want to implement a network with a MikroTik and Cisco switches.
This is the fourth post in a series that creates a Rosetta stone between IOS and RouterOS. Here are some of the others:
Click here for the first article in this series – “Cisco to MikroTik BGP command translation”
Click here for the second article in this series – “Cisco to MikroTik OSPF command translation”
Click here for the third article in the series – “Cisco to MikroTik MPLS command translation”
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
Hardware for testing
In the last article, we began using EVE-NG instead of GNS3 to emulate both Cisco IOS and RouterOS so we could compare the different commands and ensure the translation was as close as possible. However in switching, we still have to use real hardware at least in the realm of MikroTik – Cisco has IOSvL2 images that can be used in EVE-NG for switching.
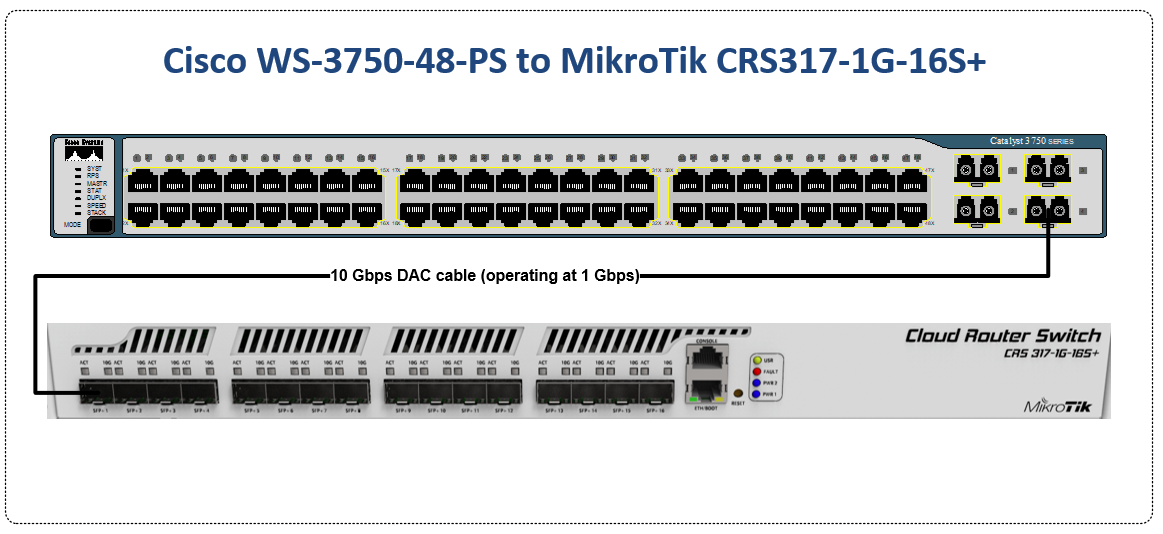
Notes on hardware bridging in the CRS series
Bridging is a very confusing topic within the realm of MikroTik equipment. It is often associated with CPU forwarding and is generally seen as something to be avoided if at all possible.
There are a few reasons for this…
1. Within routers, bridging generally does rely on the CPU for forwarding and the throughput is limited to the size of the CPU.
2. In the previous generation of CRS configuration, bridging was not the best way to configure the switch – using the port master/slave option would trigger hardware forwarding.
After MikroTik revamped the switch config for VLANs in 2018 to utilize the bridge, it more closely resembles the style of configuration for Metro Ethernet Layer 2 as well as vendors like Juniper that use the ‘bridge-domain’ style of config.
Using the bridge for hardware offload of L2 traffic
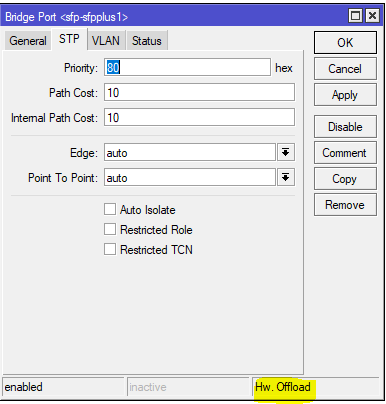
Note the Hw. Offload verification under this bridge port in the CRS317
It is important to realize that bridging in the CRS, when used for VLAN configuration is actually using the switch ASIC to forward traffic and not the CPU.
In this instance, the bridge is merely used as a familiar configuration tool to tie ports and VLANs together but does in fact allow for the forwarding of traffic in hardware at wirespeed.
Cisco to MikroTik – command translation
| Cisco command | MikroTik Command |
|---|---|
| interface FastEthernet5/0/47 switchport access vlan 100 switchport mode access end | /interface bridge port add bridge=bridge1 interface=sfp-sfpplus1 pvid=100 |
| interface GigabitEthernet5/0/4 switchport trunk encapsulation dot1q switchport trunk allowed vlan 200 switchport mode trunk end | /interface bridge vlan add bridge=bridge1 tagged=sfp-sfpplus1 vlan-ids=200 |
| interface Vlan200 ip address 172.16.1.254 255.255.255.0 end | /interface vlan add interface=bridge1 name=vlan200 vlan-id=200 /interface bridge vlan add bridge=bridge1 tagged=sfp-sfpplus1,bridge1 vlan-ids=200 /ip address add address=172.16.1.254/24 interface=vlan200 network=172.16.1.0 |
| spanning-tree mode mst | /interface bridge add fast-forward=no name=bridge1 priority=0 protocol-mode=mstp region-name=main vlan-filtering=yes |
| interface FastEthernet5/0/47 switchport access vlan 200 switchport mode access spanning-tree portfast end | interface bridge port set edge=yes-discover |
| interface GigabitEthernet5/0/4 switchport trunk encapsulation dot1q switchport trunk allowed vlan 200 switchport mode trunk channel-group 1 mode active end interface Port-channel1 switchport trunk encapsulation dot1q switchport trunk allowed vlan 200 switchport mode trunk end | interface bonding add mode=802.3ad name=Po1 slaves=sfp-sfpplus1,sfp-sfpplus3 \ transmit-hash-policy=layer-2-and-3 /interface bridge vlan add bridge=bridge1 tagged=Po1,bridge1 vlan-ids=200 |
| show mac address-table | interface bridge host print |
| show mac address-table vlan 200 | interface bridge host print where vid=200 |
| show mac address-table interface Gi5/0/4 | interface bridge host print where interface=sfp-sfpplus1 |
| show interfaces trunk show vlan | interface bridge vlan print |
| show spanning-tree | interface bridge monitor |
| show etherchannel summary | interface bonding print detail |
Examples of the MikroTik RouterOS commands from the table above
Untagged switch port
This command will create an untagged or “access” switch port on VLAN 100
[admin@MikroTik] > /interface bridge port add bridge=bridge1 interface=sfp-sfpplus1 pvid=100
Tagged switch port
This command will create a tagged or “trunk” switch port on VLAN 200. Additional VLANs can be tagged on a port by using the same syntax and adding a new VLAN number.
[admin@MikroTik] > /interface bridge vlan add bridge=bridge1 tagged=sfp-sfpplus1 vlan-ids=200
Layer 3 VLAN Interface
Similar to a Cisco SVI (but dependent on the CPU and not an ASIC) this command will create a layer 3 interface on VLAN 200
[admin@MikroTik] > /interface vlan add interface=bridge1 name=vlan200 vlan-id=200 /interface bridge vlan add bridge=bridge1 tagged=sfp-sfpplus1,bridge1 vlan-ids=200 /ip address add address=172.16.1.254/24 interface=vlan200 network=172.16.1.0
Multiple STP
This command will set the bridge loop prevention protocol to Multiple Spanning Tree. As a general observation, MSTP tends to be the most compatible across vendors as some vendors like Cisco use a proprietary version of Rapid STP.
[admin@MikroTik] > /interface bridge add fast-forward=no name=bridge1 priority=0 protocol-mode=mstp region-name=main vlan-filtering=yes
STP Edge port
This is referred to as “portfast” in the Cisco world and allows a port facing a device that isn’t a bridge or a switch to transition immediately to forwarding but if it detects a BPDU, it will revert to normal STP operation. (this is the difference between edge=yes and edge=yes-discover)
[admin@MikroTik] > /interface bridge port set edge=yes-discover
LACP Bonding
This command will create a bonding interface which is similar to a Port Channel in Cisco’s switches. Two or more physical interfaces can be selected to bond together and then the 802.3ad mode is selected which is LACP. You can also select the hashing policy and ideally it should match what the device on the other end is set for to get the best distribution of traffic and avoid interoperability issues.
[admin@MikroTik] > /interface bonding add mode=802.3ad name=Po1 slaves=sfp-sfpplus1,sfp-sfpplus3 \ transmit-hash-policy=layer-2-and-3 /interface bridge vlan add bridge=bridge1 tagged=Po1,bridge1 vlan-ids=200
View the MAC table of the switch
This print command will show all learned MAC addresses and associated VLANs in the CAM table of the switch
[admin@IPA-LAB-CRS-317] > interface bridge host print Flags: X - disabled, I - invalid, D - dynamic, L - local, E - external # MAC-ADDRESS VID ON-INTERFACE BRIDGE AGE 0 DL 64:D1:54:F0:0E:46 Po1 bridge1 1 DL 64:D1:54:F0:0E:47 sfp-sfpplus2 bridge1 2 D E 04:FE:7F:5C:5D:9C 1 Po1 bridge1 3 DL 64:D1:54:F0:0E:46 1 Po1 bridge1 4 D 00:0C:42:B2:A6:3D 200 sfp-sfpplus2 bridge1 52s 5 D E 4C:5E:0C:23:DF:50 200 Po1 bridge1 6 DL 64:D1:54:F0:0E:46 200 bridge1 bridge1 7 DL 64:D1:54:F0:0E:47 200 sfp-sfpplus2 bridge1
View the MAC table for VLAN 200 in the switch
This print command will show all learned MAC addresses in VLAN 200.
[admin@IPA-LAB-CRS-317] > interface bridge host print where vid=200 Flags: X - disabled, I - invalid, D - dynamic, L - local, E - external # MAC-ADDRESS VID ON-INTERFACE BRIDGE AGE 0 D 00:0C:42:B2:A6:3D 200 sfp-sfpplus2 bridge1 51s 1 D E 4C:5E:0C:23:DF:50 200 Po1 bridge1 2 DL 64:D1:54:F0:0E:46 200 bridge1 bridge1 3 DL 64:D1:54:F0:0E:47 200 sfp-sfpplus2 bridge1
View the MAC table for bonding interface Po1 in the switch
This print command will show all learned MAC addresses on port Po1.
[admin@IPA-LAB-CRS-317] > interface bridge host print where interface=Po1 Flags: X - disabled, I - invalid, D - dynamic, L - local, E - external # MAC-ADDRESS VID ON-INTERFACE BRIDGE AGE 0 DL 64:D1:54:F0:0E:46 Po1 bridge1 1 D E 04:FE:7F:5C:5D:9C 1 Po1 bridge1 2 DL 64:D1:54:F0:0E:46 1 Po1 bridge1 3 D E 4C:5E:0C:23:DF:50 200 Po1 bridge1
View the current VLANs configured in the switch
The bridge vlan print command will show all configured VLANs in the switch.
[admin@IPA-LAB-CRS-317] > interface bridge vlan print
Flags: X - disabled, D - dynamic
# BRIDGE VLAN-IDS CURRENT-TAGGED CURRENT-UNTAGGED
0 bridge1 200 bridge1 sfp-sfpplus2
Po1
1 D bridge1 1 bridge1
Po1View Bridge Spanning Tree information
The bridge monitor command will show the configuration details and current state of spanning tree including the root bridge and root port
[admin@IPA-LAB-CRS-317] > interface bridge monitor
numbers: 0
state: enabled
current-mac-address: 64:D1:54:F0:0E:46
root-bridge: yes
root-bridge-id: 0.64:D1:54:F0:0E:46
regional-root-bridge-id: 0.64:D1:54:F0:0E:46
root-path-cost: 0
root-port: none
port-count: 2
designated-port-count: 2
mst-config-digest: ac36177f50283cd4b83821d8ab26de62LACP Bonding information
This command will show the details of the LACP configuration and whether the bonding interface is running which indicates a valid LACP neighbor.
[admin@IPA-LAB-CRS-317] > interface bonding print detail
Flags: X - disabled, R - running
0 R name="Po1" mtu=1500 mac-address=64:D1:54:F0:0E:46 arp=enabled arp-timeout=auto
slaves=sfp-sfpplus1,sfp-sfpplus3 mode=802.3ad primary=none link-monitoring=mii
arp-interval=100ms arp-ip-targets="" mii-interval=100ms down-delay=0ms up-delay=0ms
lacp-rate=30secs transmit-hash-policy=layer-2-and-3 min-links=0