In the world of network engineering, learning a new syntax can challenging especially if you need a lot of detail quickly. The command structure for RouterOS can be a bit challenging sometimes if you are used to Cisco CLI commands. Most of us that have been in networking for a while got our start with Cisco gear and so it is helpful to draw comparisons between the commands, especially if you are trying to build a network with a MikroTik and Cisco router.
This is the first post in a series I’ve wanted to do for a while that creates a Rosetta stone essentially between IOS and RouterOS. We plan to tackle a number of other command comparisons like OSPF, MPLS and VLANs to make it easier for network engineers trained in Cisco IOS to successfully implement MikroTik / RouterOS devices. While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
We plan to tackle a number of other command comparisons like OSPF, MPLS and VLANs to make it easier for network engineers trained in Cisco IOS to successfully implement Mikrotik / RouterOS devices.
Using GNS for testing
We used GNS3 to emulate both Cisco IOS and RouterOS so we could compare the different commands and ensure the translation was as close as possible.
BGP Commands
| Cisco Command | MikroTik Command |
|---|---|
| show ip bgp summary | routing bgp peer print brief |
| show ip bgp neighbor | routing bgp peer print status |
| show ip bgp neighbor 1.1.1.1 advertised-routes | routing bgp advertisements print peer=peer_name |
| show ip bgp neighbor 1.1.1.1 received-routes | ip route print where received-from=peer_name |
| show ip route bgp | ip route print where bgp=yes |
| clear ip bgp 172.31.254.2 soft in | routing bgp peer refresh peer1 |
| clear ip bgp 172.31.254.2 soft out | routing bgp peer resend peer1 |
| BGP-Cisco(config)#router bgp 1 | /routing bgp instance set default as=2 |
| BGP-Cisco(config-router)#neighbor 172.31.254.2 remote-as 2 | /routing bgp peer add name=peer1 remote-address=172.31.254.1 remote-as=1 |
| BGP-Cisco(config-router)#network 100.99.98.0 mask 255.255.255.0 BGP-Cisco(config-router)#network 100.99.97.0 mask 255.255.255.0 BGP-Cisco(config-router)#network 100.99.96.0 mask 255.255.255.0 | /routing bgp network add network=100.89.88.0/24 add network=100.89.87.0/24 add network=100.89.86.0/24 |
| BGP-Cisco(config)#router bgp 1 BGP-Cisco(config-router)#neighbor 172.31.254.2 default-originate | /routing bgp peer add default-originate=always name=peer1 remote-address=172.31.254.1 remote-as=1 |
Examples of the MikroTik RouterOS commands from the table above
[admin@BGP-MikroTik] > routing bgp peer print brief
This is a quick way to get a list of peers/AS and their status
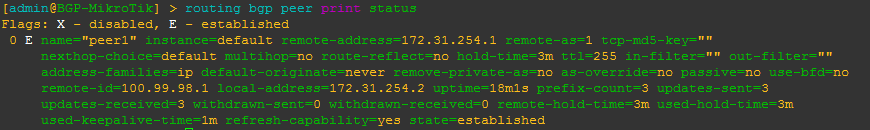
[admin@BGP-MikroTik] > routing bgp peer print status
This is a command that will give you more detailed information about a BGP peer including MD5 auth, timers, prefixes received and the state of the peering as well as other info.
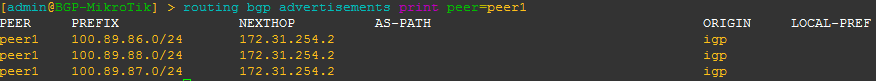
[admin@BGP-MikroTik] > routing bgp advertisements print peer=peer_name
This will allow you to see what BGP prefixes are actually being advertised to a peer and the nexthop that will be advertised
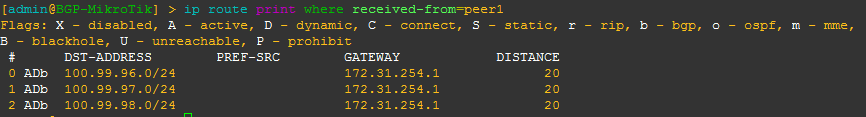
[admin@BGP-MikroTik] > ip route print where received-from=peer_name
This will allow you to see what BGP prefixes are actually being received from a peer and the nexthop that will be advertised
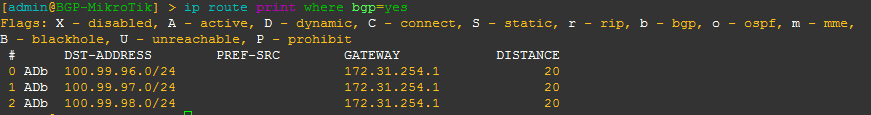
[admin@BGP-MikroTik] > ip route print where bgp=yes
This will allow you to see what all BGP prefixes that are in the routing table – both active and not. This is a slight difference between Cisco and MikroTik since Cisco keeps BGP routes that aren’t in the routing table in the bgp table, whereas MikroTik routers keep all routes in the routing table with a distinction between active and not.
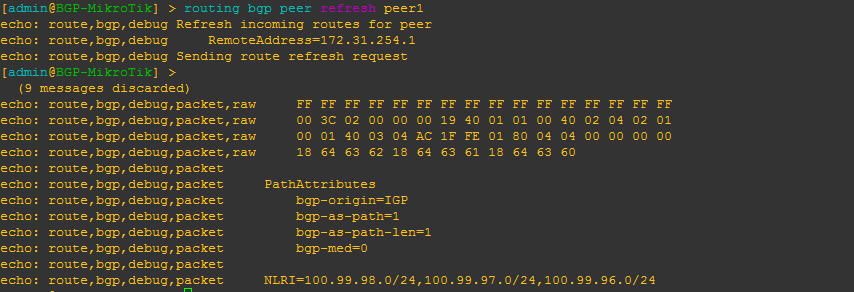
[admin@BGP-MikroTik] > routing bgp peer refresh peer_name
This will allow you to force the BGP peer to resend all prefixes without tearing down the peering – similar to a soft clear in Cisco IOS.
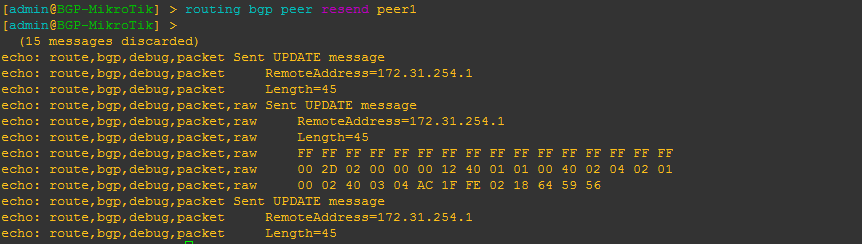
[admin@BGP-MikroTik] > routing bgp peer resend peer_name
This will allow you to force RouterOS to resend all prefixes to the peer without tearing down the peering – similar to a soft clear in Cisco IOS.
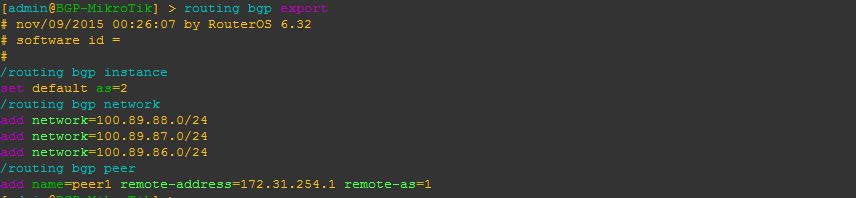
Configure BGP instance and peering
Here is a very basic BGP peering config with the minimum required to get BGP running for RouterOS. It includes setting the BGP AS, a peering and several networks to advertise.
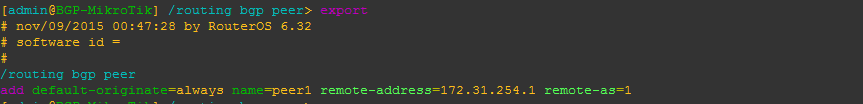
Originate a default route to a specific peer
This will configure the peering to originate or advertise a 0.0.0.0/0 route to the peer regardless of whether or not a default route already exists in the routing table. You can use the alternate default-originate=if-installed to only advertise a default route if one exists in the routing table.
More to come
There are so many commands to consider for BGP, we probably could have added close to 100, but we decided to list the commands we use the most often to start with and will be adding to the list of BGP commands as well as others like OSPF, MPLS and VLANs in future posts.